Vanguard is no longer being actively developed. Development has moved to Phoenix which has a completely rewritten codebase to allow more advanced features and better performance.
Vanguard is a full-fledged SIEM with endpoint agents, SOAR, integrations and attack surface monitoring. The frontend is built with TypeScript on Next.js and the backend is built with TypeScript on Node. Endpoint agents are built, depending on the version with Rust or C#.
For a long time I have wanted to collect all the logs and alerts from my home network and servers into a single platform. Despite trying various open-source options, I couldn’t find one that met all my requirements. This led me to develop Vanguard. It incorporates all the functionalities I’ve come to expect from enterprise-grade solutions such as Splunk and Palo Alto Cortex, yet it’s cost-effective to operate.
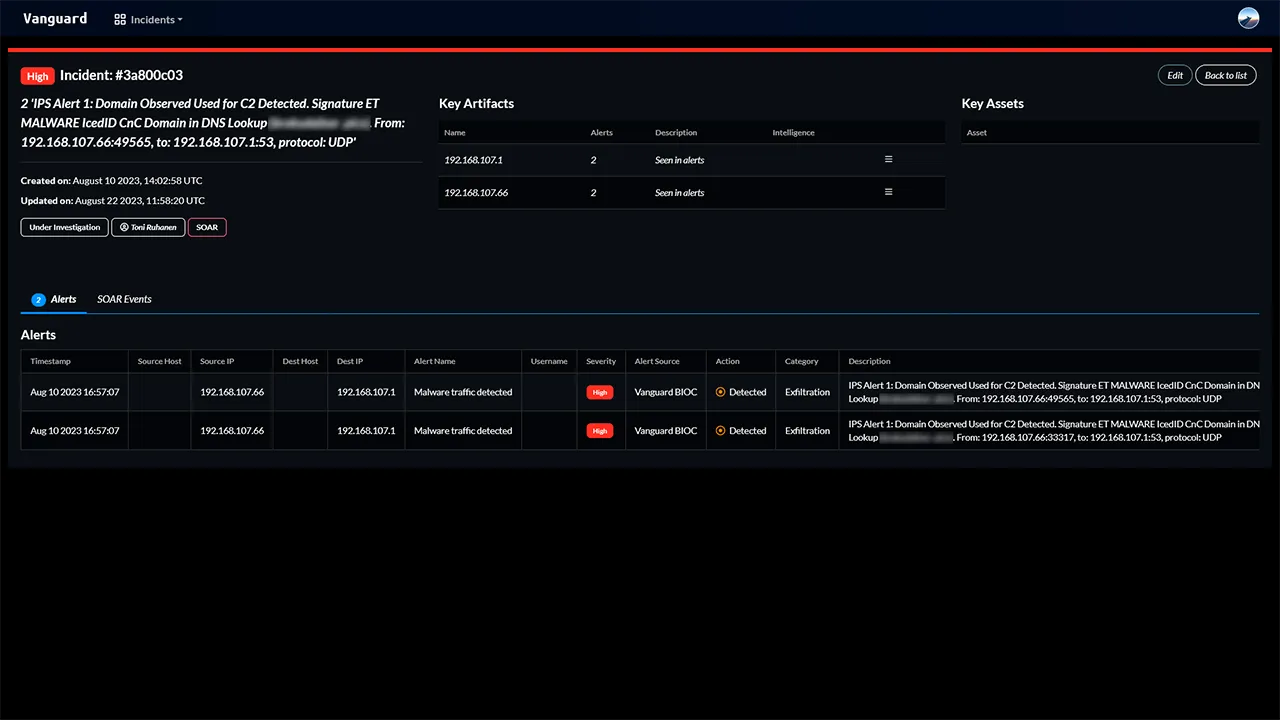
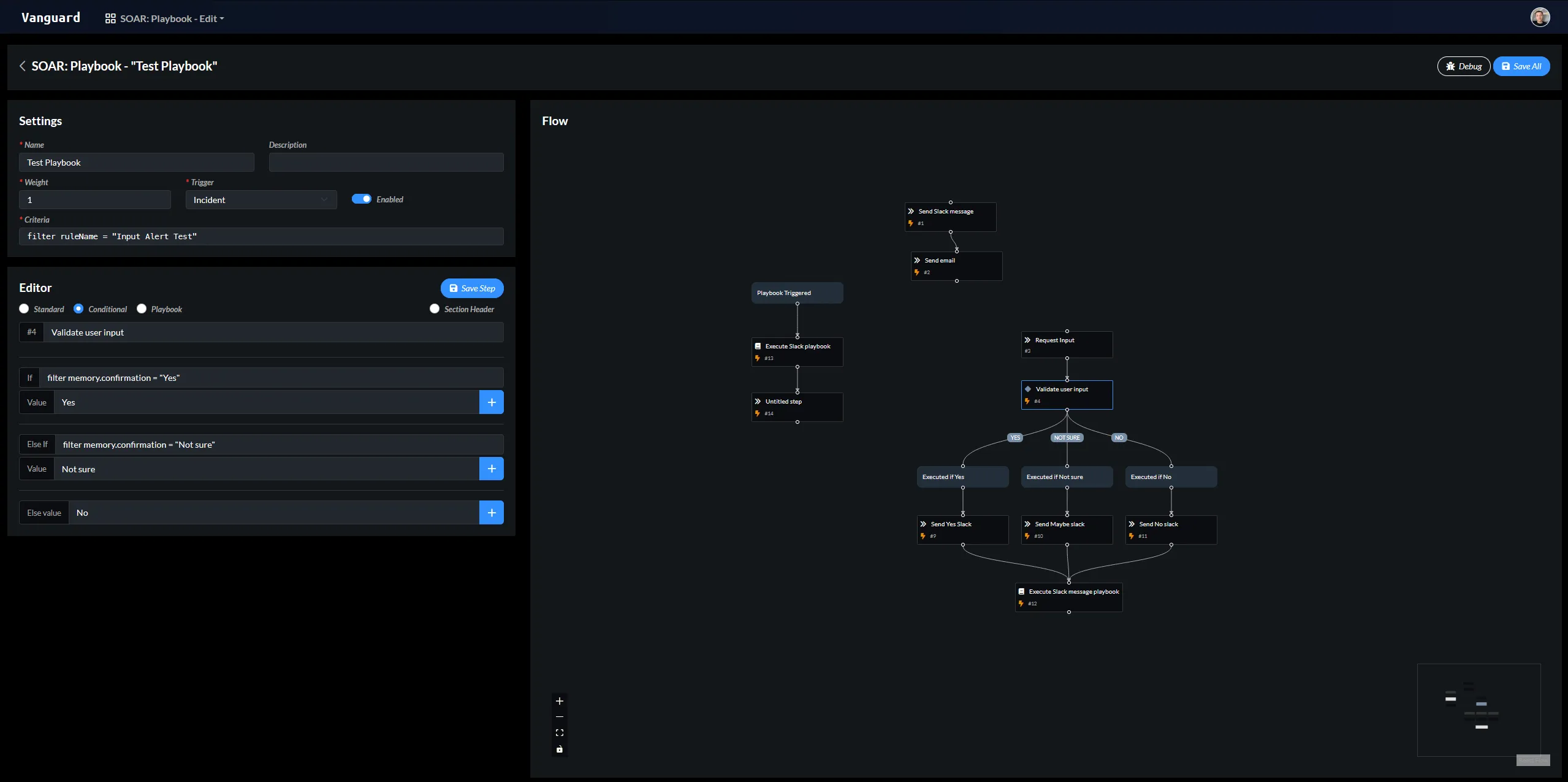
Automating incident response
One of the most important features of Vanguard is the SOAR. It allows the automation of almost anything, but most importantly handling incidents. This means that before an analyst even sees the incident, Vanguard has already enriched, investigated and resolved the incident. According to my tests, the average time to handle an incident from the moment it is detected is less than 45 seconds. Vanguard also includes a visual playbook editor, which makes it easy to create and modify playbooks.
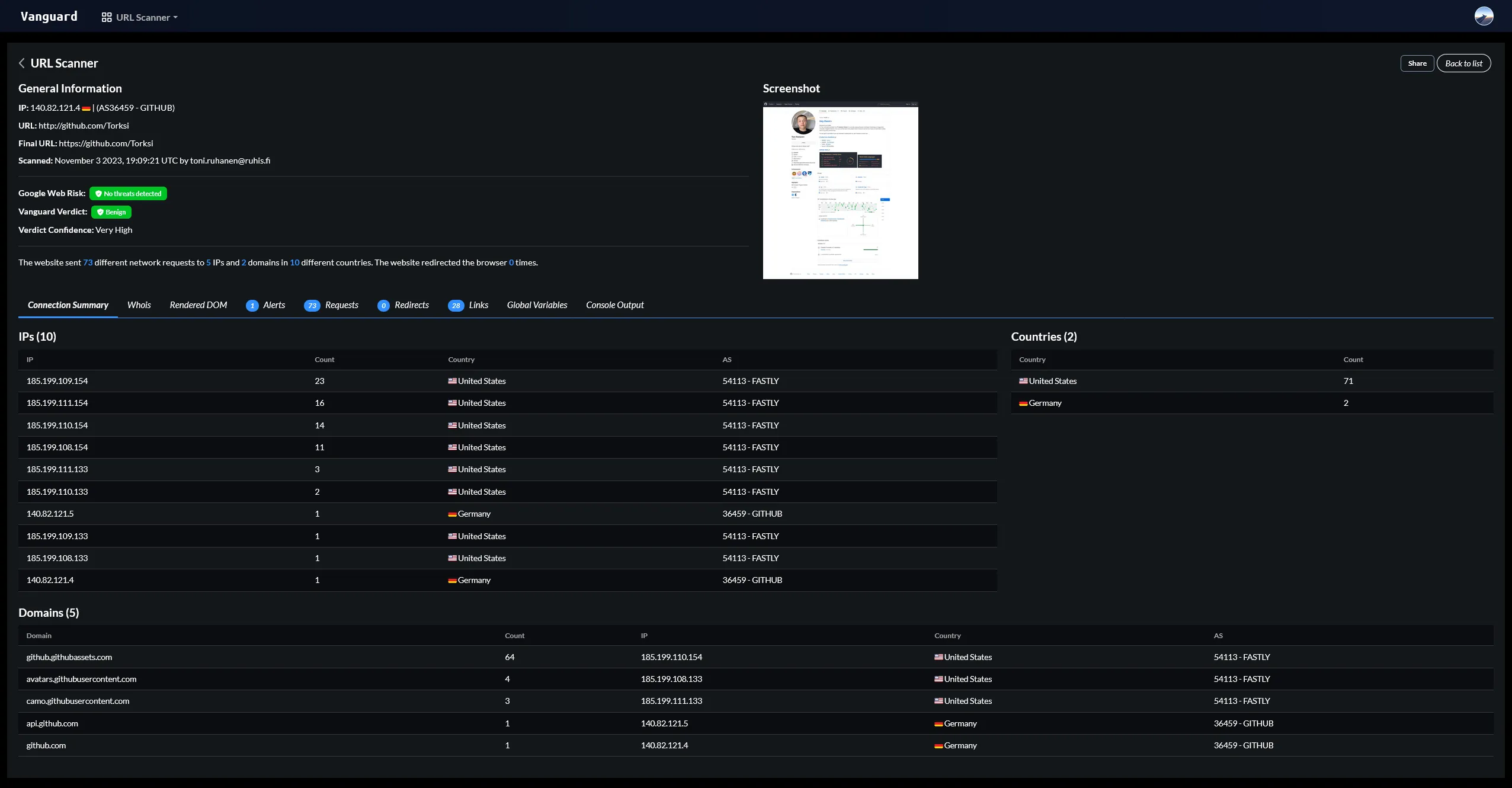
Analyzing suspicious websites
I had previously created a tool called urlcheck, which I used to analyze suspicious websites. I integrated this tool into Vanguard to make it easier to analyze suspicious URLs. The scanning algorithm is drastically improved compared to the original publicly available version and it is now capable of detecting phishing sites with a high accuracy. The new version also allows email submissions and integration with SOAR for automated analysis and response.
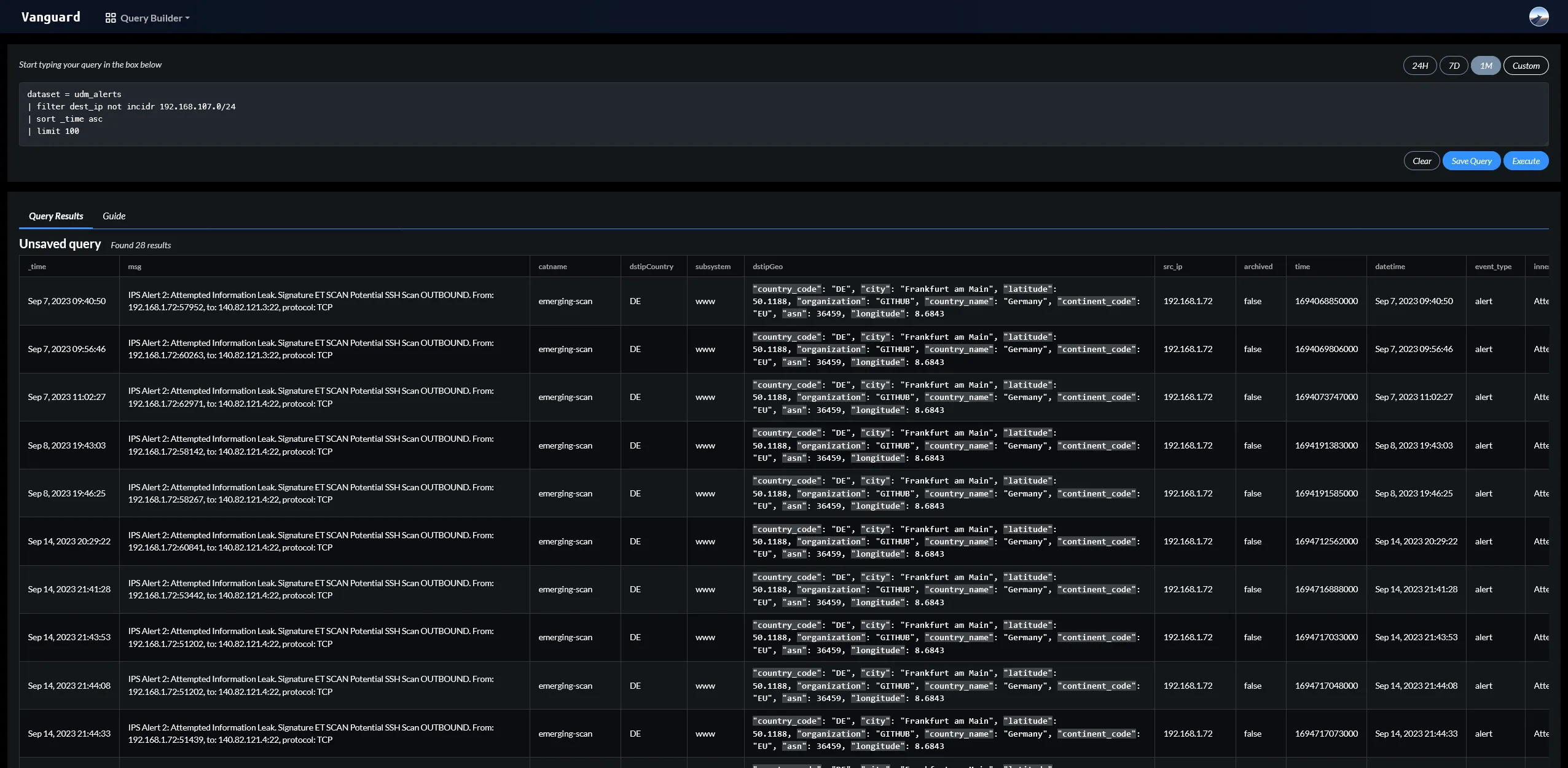
Centralised log collection and analysis
Vanguard is capable of collecting logs from almost any source. It has built-in support for syslog, Windows Event Log, and many other sources. It can also collect logs from custom sources using the HTTP API. Once the logs have been collected, they are parsed and normalized into a common format. This allows Vanguard to easily analyze and correlate logs from different sources. The logs can easily be queried using RQL which was specifically designed for this project.
After the normalizing, Vanguard runs the logs through a set of IOCs to detect possible threats. If an IOC is detected, Vanguard will automatically raise an alert and take the necessary actions.
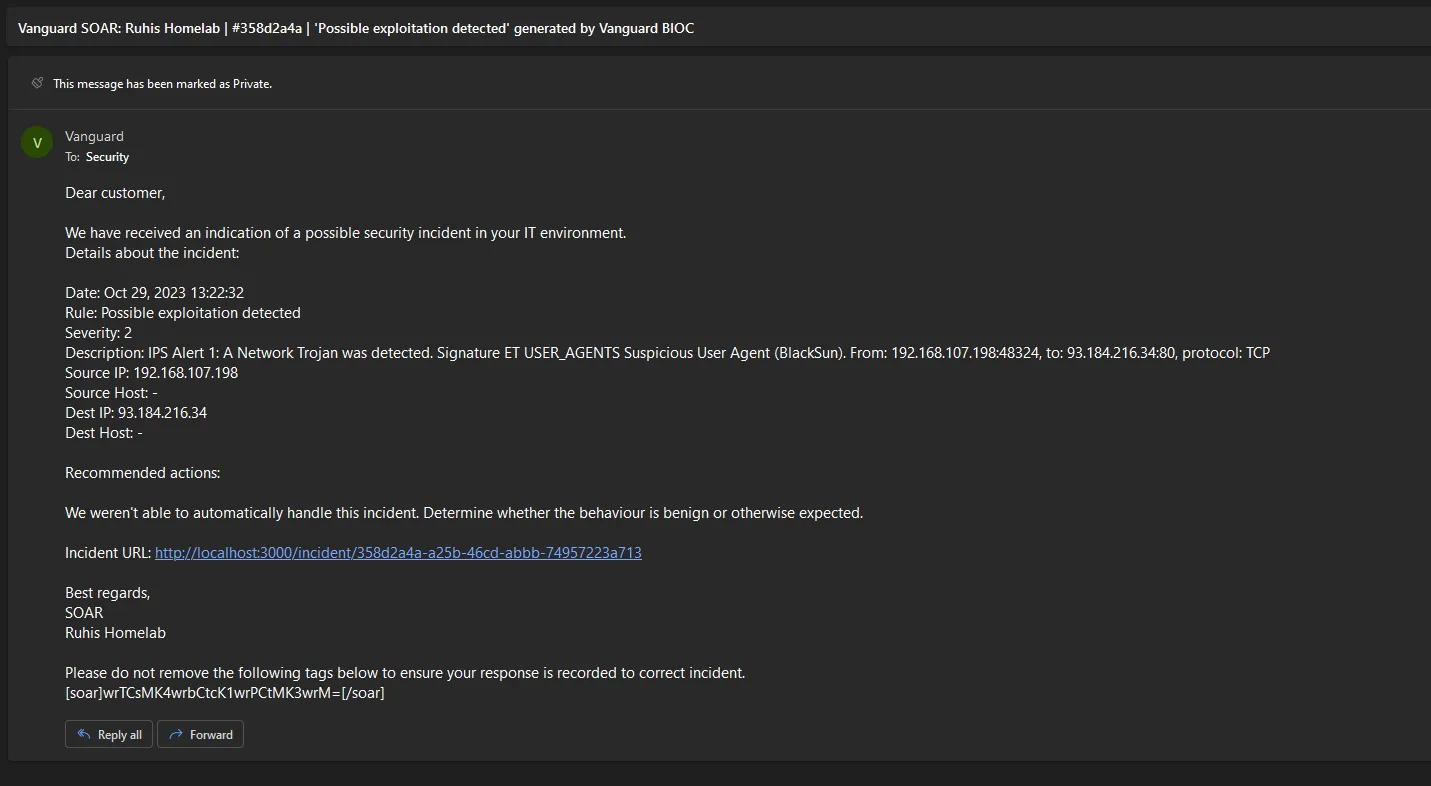
Email Integration
Vanguard has a built-in email integration that allows sending and receiving of emails. This is useful for example when an analyst needs to communicate with the end-user. Vanguard SOAR is also able to use this integration to notify the analyst, if there is a need for manual intervention.
Vanguard also allows IOC rules to be applied to emails. This means that if an email contains an IOC, Vanguard will automatically raise an alert or incident. After the incident has been created, Vanguard SOAR playbooks can be used to handle the incident.
Technical stuff
The majority of Vanguard’s codebase is implemented in TypeScript, except for the endpoint agents, which are crafted in Rust and C#. For data management, I opted for PostgreSQL, while Elasticsearch is used for log storage.
Currently the Vanguard backend is running on a single server, but I have been planning to make it more scalable by splitting some components like SOAR and log ingestion to their own servers. This would allow the system to scale better and handle more load. Both the frontend and backend are running on Docker, which makes it easy to deploy and update the system.