Phoenix is a complete rewrite of the original Vanguard. It’s still the same feature rich SIEM with all the functionalities of the original version, but with much more advanced features like context aware incident response, automated threat hunting, and more.
Initially I wanted to continue developing the original version of Vanguard, but I quickly realized that it would be much easier to start from a clean slate. This allowed me to rethink the architecture and implement new features that were not possible with the original version or would have required a lot of work to implement.
Context aware incident response
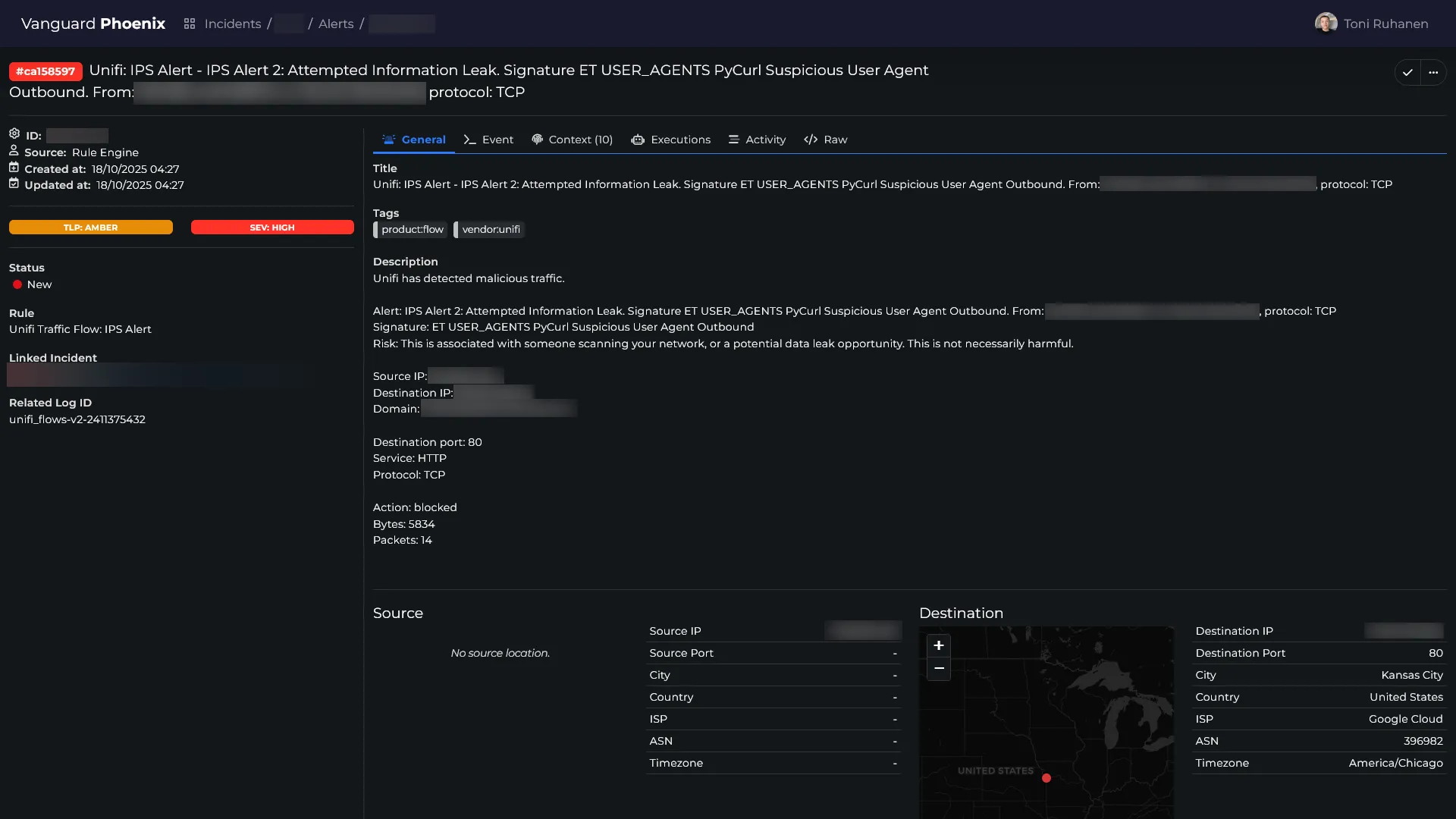
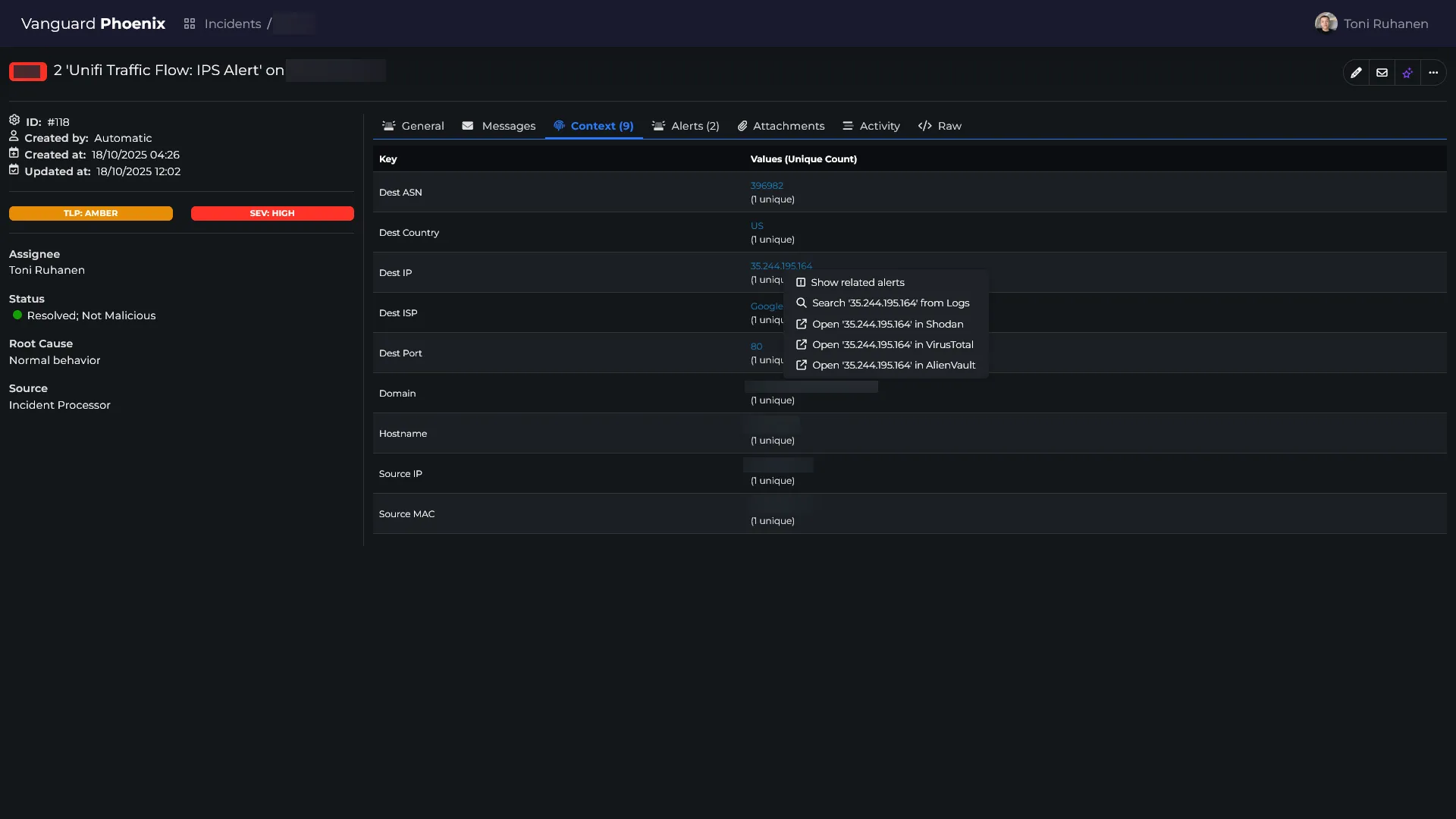
One of the biggest improvements in Phoenix is the context aware incident response. This means that Phoenix is able to automatically enrich alerts with additional context, such as the user’s role, geographical location, threat intelligence, and more. This allows Phoenix to make more informed decisions automatically, without the need for human intervention.
Automating incident response
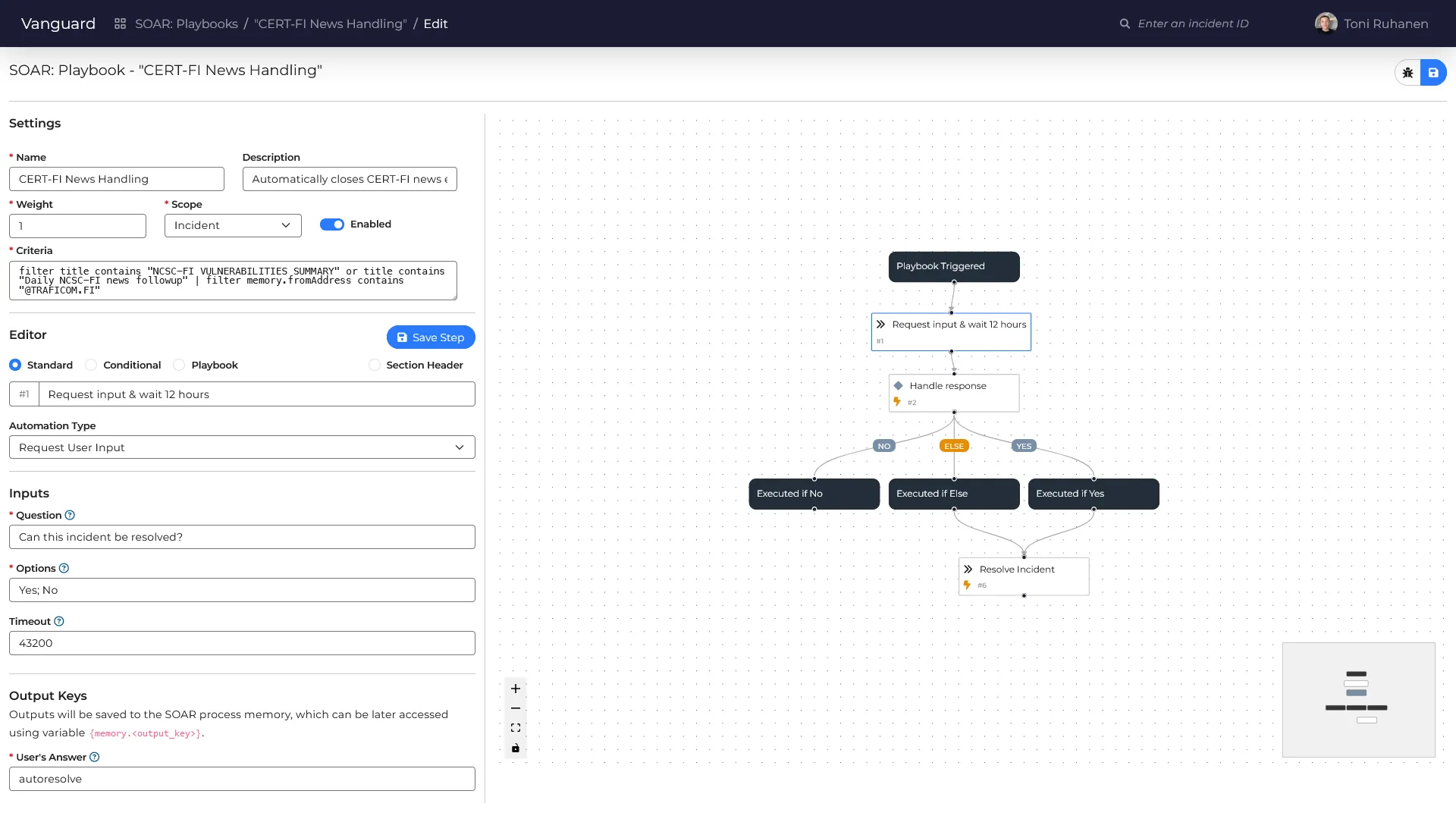
One of the most important features of Phoenix is the SOAR. It allows the automation of almost anything, but most importantly handling alerts. This means that before an analyst even sees the alert, Phoenix has already enriched, investigated, and in most cases, resolved it. According to my tests, the average time to handle an incident from the moment it is created is less than 45 seconds.
Centralised log collection and analysis
Phoenix is capable of collecting logs from almost any source. It has built-in support for syslog, Windows Event Log, multiple firewall vendors, and many other sources. It can also collect logs from custom sources using the HTTP API. Once the logs have been collected, they are parsed and normalized into a common format. This allows Phoenix to easily analyze and correlate logs from different sources. The logs can easily be queried using RQL which was specifically designed for this project. Phoenix’s log analysis tool is also used in my public Log Analysis Tool.
After the normalizing, Phoenix runs the logs through a set of IOCs to detect possible threats. If an IOC is detected, Phoenix will automatically raise an alert and take the necessary actions.
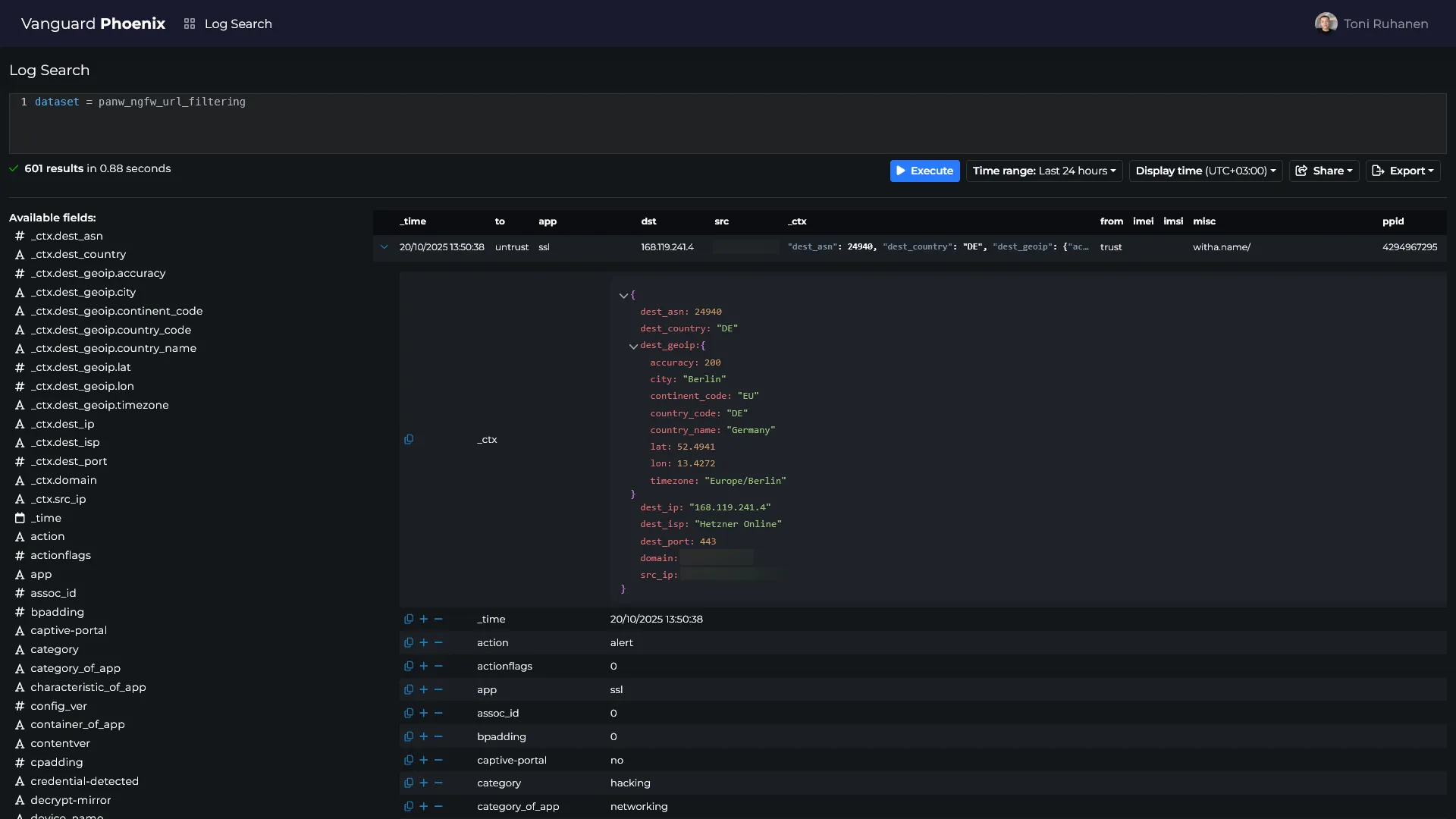
Analyzing suspicious websites
I had previously created a tool called urlcheck, which I used to analyze suspicious websites. I integrated this tool into Phoenix to make it easier to analyze suspicious URLs. The scanning algorithm is drastically improved compared to the original publicly available version and it is now capable of detecting phishing sites with a high accuracy. The new version also allows email submissions and integration with SOAR for automated analysis and response.
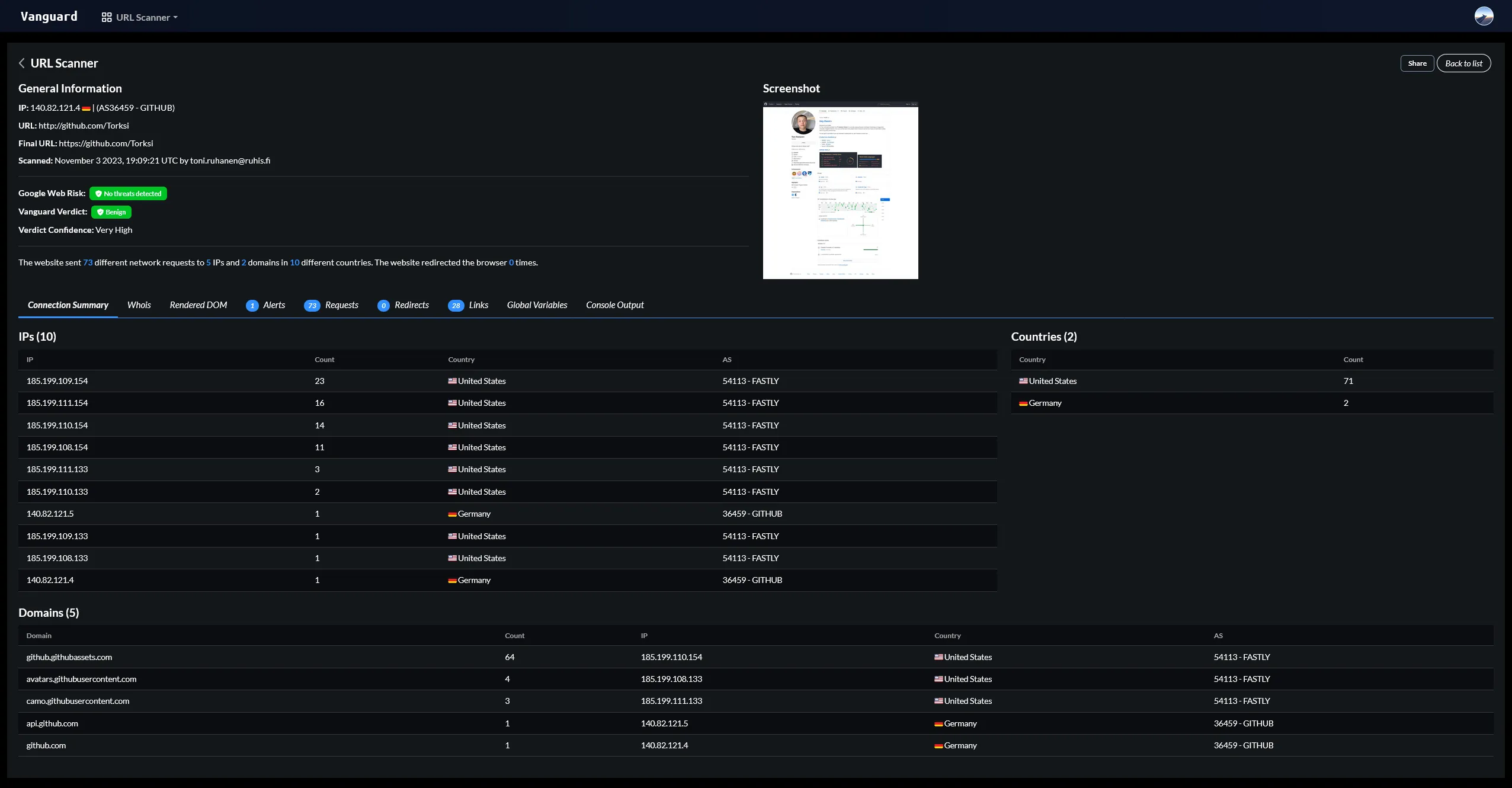
Detections as Code
Phoenix provides a way to manage detections as code. This means that detection rules can be stored in a Git repository, which allows for version control, collaboration, and easy deployment. Detection rules are written in a simple YAML format, but can include more complex logic using JavaScript.
Email Integration
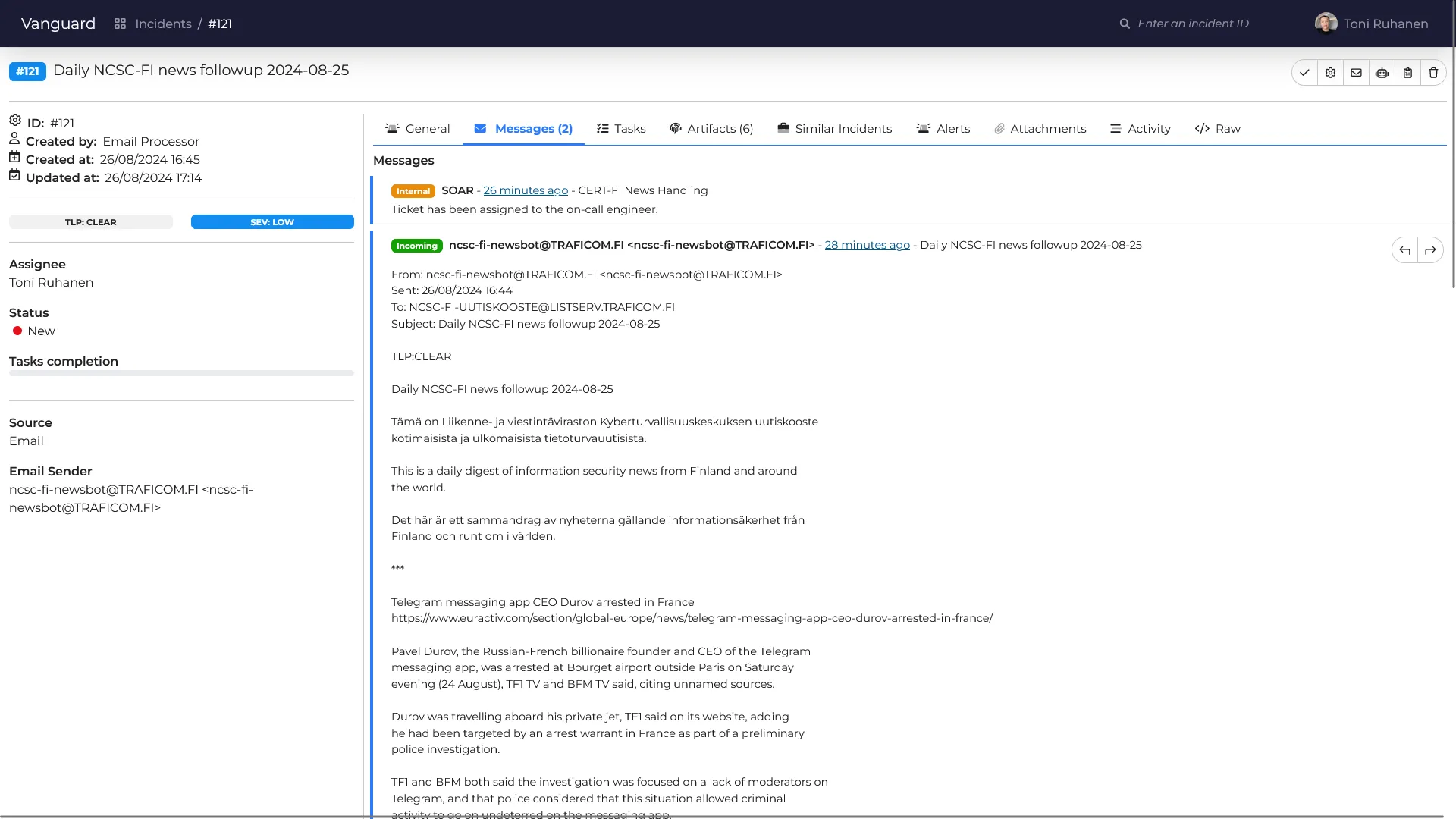
Phoenix has a built-in email integration that allows sending and receiving of emails. This is useful for example when an analyst needs to communicate with the end-user. Phoenix SOAR is also able to use this integration to notify the analyst, if needed.
Incoming emails will automatically get necessary tags and TLP levels assigned based on some predefined rules. This makes it easier to see which emails are important and which are not.